Critical Infrastructure Still at High Risk: Forescout Research Spotlights 21 New Vulnerabilities
06.12.2023 - 09:02:59Critical Infrastructure Still at High Risk: Forescout Research Spotlights 21 New Vulnerabilities. Impact includes popular routers, open-source components used to connect critical local networks in energy, healthcare, transportation and emergency services
Forescout, a global cybersecurity leader, today released “SIERRA:21 – Living on the Edge,” an analysis of 21 newly discovered vulnerabilities within OT/IoT routers and open-source software components. The report — produced by Forescout Research – Vedere Labs, a leading global team dedicated to uncovering vulnerabilities in critical infrastructure — emphasizes the continued risk to critical infrastructure and sheds light on possible mitigations.
This press release features multimedia. View the full release here: https://www.businesswire.com/news/home/20231205915662/en/
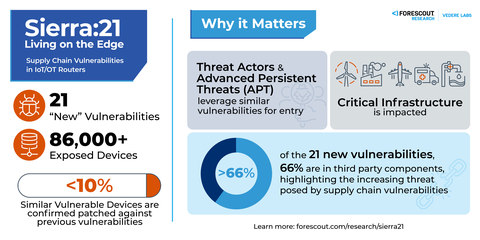
Sierra:21 Infographic (Source: Forescout)
Read the blog: Forescout Vedere Labs discloses 21 new vulnerabilities affecting OT/IoT routers
Forescout Research further finds:
- The attack surface is expansive with 86,000 vulnerable routers still exposed online. Less than 10% of these routers are confirmed to be patched against known previous vulnerabilities found since 2019.
- Regions with the highest number of exposed devices includes:
- 68,605 devices in The United States
- 5,580 devices in Canada
- 3,853 devices in Australia
- 2,329 devices in France
- 1,001 devices in Thailand
- Among the 21 vulnerabilities, one has critical severity (CVSS score 9.6), nine have high severity and 11 have medium severity. These vulnerabilities allow attackers to steal credentials, take control of a router by injecting malicious code, persist on the device and use it as an initial access point into critical networks.
- Patching can’t fix everything. 90 percent of devices exposing a specific management interface have reached end of life, meaning they cannot be further patched.
- It’s an uphill battle to secure supply chain components. Open-source software elements continue to go unchecked and increase the attack surface of critical devices, leading to vulnerabilities that may be hard for organizations to track and mitigate.
“We are raising the alarm today because there remain thousands of OT/IoT devices representing an increased attack surface that requires attention,” advises Elisa Constante, VP of Research, Forescout Research – Vedere Labs. “Vulnerabilities impacting critical infrastructure are like an open window for bad actors in every community. State-sponsored actors are developing custom malware to use routers for persistence and espionage. Cybercriminals are also leveraging routers and related infrastructure for residential proxies and to recruit into botnets. Our discoveries reaffirm the need for heightened awareness of the OT/IoT edge devices that are so often neglected.”
Sierra Wireless and OpenDNS have issued patches for the identified vulnerabilities. TinyXML is an abandoned open source project, so the upstream vulnerabilities will not be fixed and must be addressed downstream.
For more information, download the full report, “SIERRA:21 – Living on the Edge,” now at https://www.forescout.com/resources/sierra21-vulnerabilities.
Additional Resources:
- View the on-demand webinar: https://www.brighttalk.com/central/account/616385/channel/13809/video/602171
- Read more insight from Forescout Research: Hacktivists attack U.S. water treatment plant – analysis and implications
About Forescout
Forescout Technologies, Inc., a global cybersecurity leader, continuously identifies, protects and helps ensure the compliance of all managed and unmanaged connected cyber assets – IT, IoT, IoMT and OT. For more than 20 years, Fortune 100 organizations and government agencies have trusted Forescout to provide vendor-agnostic, automated cybersecurity at scale. The Forescout® Platform delivers comprehensive capabilities for network security, risk and exposure management, and extended detection and response. With seamless context sharing and workflow orchestration via ecosystem partners, it enables customers to more effectively manage cyber risk and mitigate threats.
View source version on businesswire.com: https://www.businesswire.com/news/home/20231205915662/en/

